Penetration Testing: Why It’s Critical to Your IT Security
Connectria
Author
Date
July 28, 2022

Finding and remediating your business’ security flaws is imperative to protecting not only your data but also your reputation. Over the last decade, external and internal penetration testing has become increasingly important to reduce risks.
Assessing your security posture for vulnerabilities is even more essential now as ransomware is more rampant than ever.
Penetration testing shouldn’t be an afterthought. If your organization has made significant changes to your infrastructure or network and/or recently applied security patches, penetration testing should be conducted to ensure vulnerabilities have been fully addressed.
What is Penetration Testing?
Penetration testing is a security process that involves a benevolent party’s attempt to access or break into your system. It can be a helpful exercise to evaluate your environment or application for vulnerabilities.
This can include threats such as a bad actor, cyberattacks, or other potential hacking. This process is sometimes referred to as ‘ethical hacking’, a ‘white hat attack’, or simply a ‘pen test’. A pen test can unearth a variety of potential vulnerabilities from configuration errors to potential design flaws, security gaps, or software bugs.
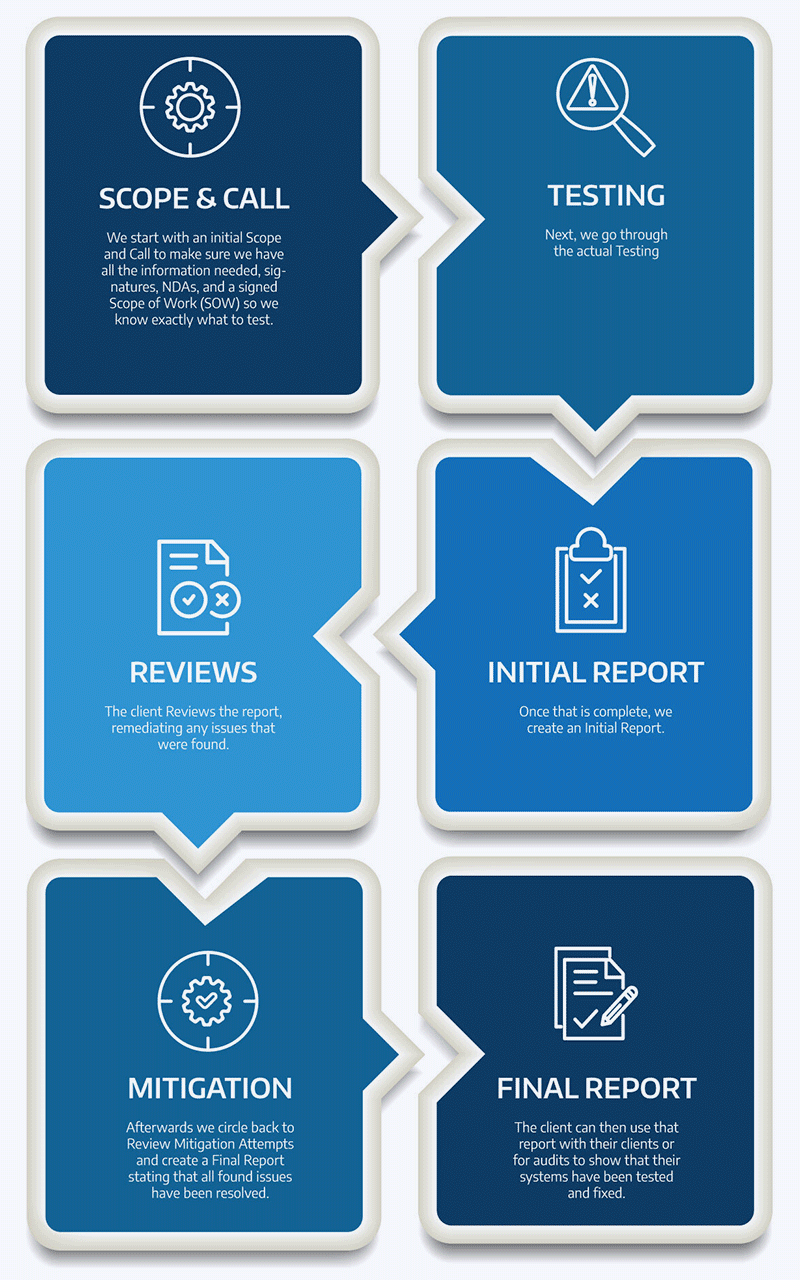
Connectria’s 6 Step Penetration Testing Process
Connectria provides application and network layer pen testing and remediation to help close security gaps and minimize threat exposure in your infrastructure.
Want to strengthen your security posture with penetration testing?
Security Assessments
Penetration testing is a subcategory of a security assessment. There are many different types of frameworks available ranging from basic to in-depth assessments. The National Institute for Standards and Technology (NIST), for example, is a government-based organization that creates security standards. NIST has a variety of frameworks including:
- Cybersecurity
- Common Industry Format (CIF)
- SP 800-53
- SP 800-171
These tests provide a lot more controls and sub-controls for larger enterprise businesses. However, if you’re a small to medium-sized business wanting to secure your systems but have limited staff and need to start somewhere, start with the cybersecurity framework and the Center for Internet Security (CIS) Top 18. Once security is in place, then you can expand into bigger frameworks to go deeper in securing more of your systems (800-171 and 800-53).
There are also industry and vertical-specific security tests. For example, if you’re a financial services business and you have web applications for customers to use for financial records, you would leverage a SOC2 audit. This audit assesses a provider’s ability to ensure the security, availability, integrity, confidentiality, and privacy of their customers’ data. This report is highly relevant to those who are concerned about security and compliance. SOC 2 is broken down into two types of reports:
- Type I – assesses the provider’s systems and protocols at a point in time. The auditor will review how the controls are designed and evaluate their suitability. This report is good, but SOC 2 Type II is more informative.
- Type II – looks at the effectiveness of these controls by assessing them over a minimum of six months. Essentially, SOC 2 Type II validates that the controls are in place and that protocols are consistently followed.
Learn more about our Cloud Security & Compliance Support here.
How Can You Benefit from Penetration Testing?
The primary benefit of penetration testing is giving you and your entire organization peace of mind when it comes to security.
Management and C-Level Security Officers (CSOs) are required to report their efforts to secure company systems. Penetration testing is a good practice to discover vulnerabilities. Other benefits include security assurance, not just for your internal stakeholders, but also for your external stakeholders and customers.
Some industries require third-party audits and some of those audits require pen testing. Also, a lot of compliances require pen testing, such as PCI and even some of the smaller frameworks. Ultimately, a pen test provides proof that you are doing what you say you are as it relates to claims of monitoring web applications, testing systems, patching vulnerabilities, and performing regular updates.
Staying Secure Post-Testing
Once a penetration test is complete, the customer reviews the report, remediates any found vulnerabilities, and ensures they keep up with updates, patching, and making changes at an appropriate cadence.
This stage is not associated with penetration testing procedures, but rather my recommendation. The penetration testing report can open your eyes to potential vulnerabilities. However, nothing will change unless you make the necessary changes and establish protocols to keep up with potential future vulnerabilities.
We recommend annual penetration testing. Additionally, you can perform vulnerability scanning quarterly to keep up with patching and updates.
Getting Started with Pen Testing
Connectria Professional Services can perform penetration testing as well as remediate your vulnerabilities. We can help you achieve and maintain compliance by performing comprehensive penetration testing in both application and network layers, keeping your business-critical systems safe and secure.
Keep Reading
Prepare for the future
Tell us about your current environment and we’ll show you the best path forward.
Fast track your project. Give us a call.






