Compliance in AWS: Locking Down Resources
Connectria
Author
Date
May 25, 2021

We recently discussed architectural principles to help you keep your AWS environments secure and compliant. Additionally, we examined these principles alongside the role of the Health Information Trust Alliance (HITRUST) certification.
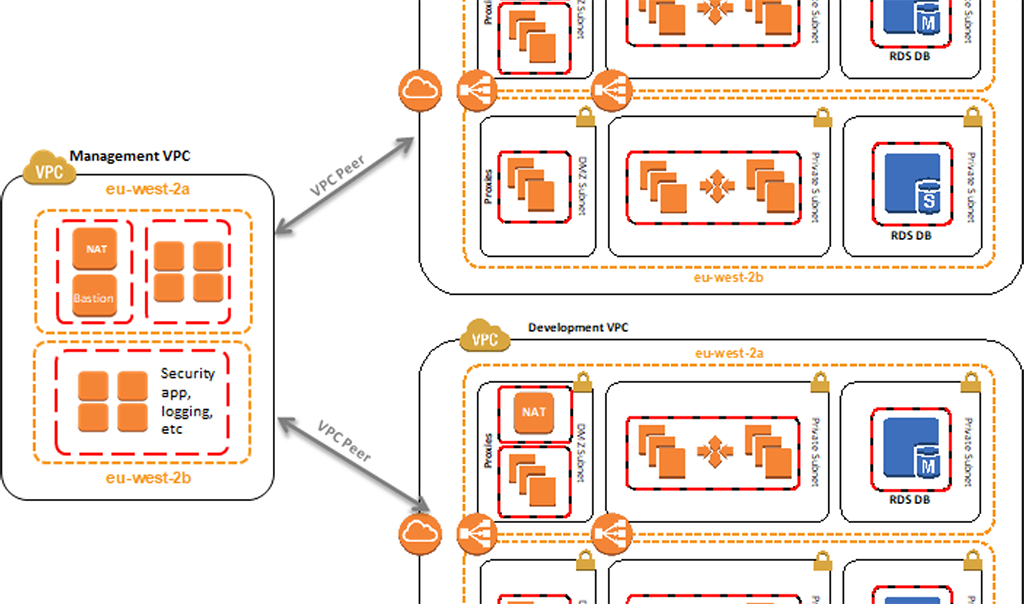
In my last article, I looked at resource segregation which limits the scope of PHI and prevents leaks while developing. To summarize, a primary consideration around resource segregation is to ensure that you’re separating resources between nonproduction and production environments. Part of HIPAA and HITRUST certifications is that you cannot have overlapping resources between production and non-production.
IAM Policies
Another common issue that we find with our customers is locking down resources. There are several different strategies we can take to ensure we are locking down our resources.
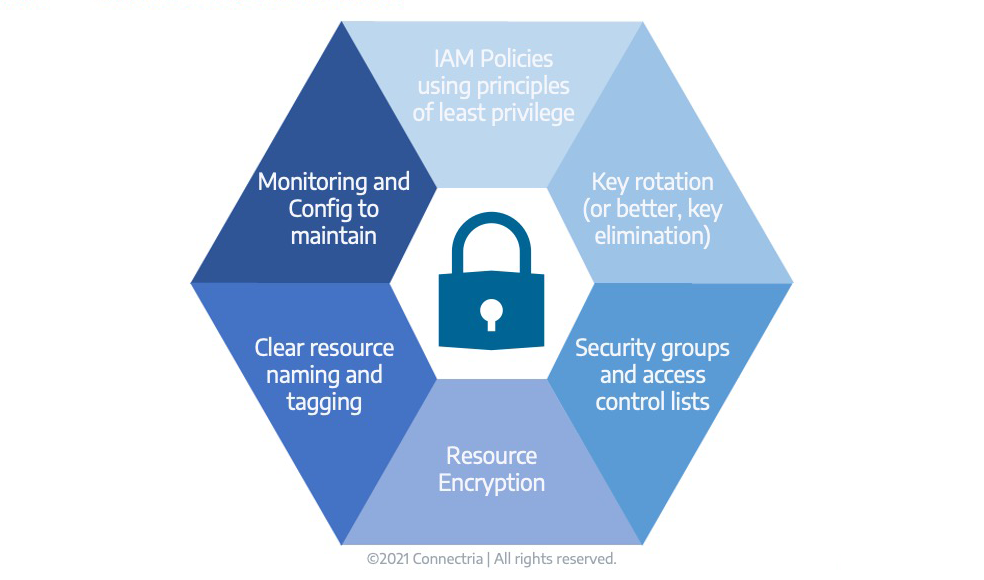
Above are a few architecture considerations to consider. The first focuses on using your IAM policies within AWS to ensure you’re following the principles of least privilege. This ensures that your users only have access to the resources and tools within AWS they need to complete their job.
Key Rotation
Ideally, you’re not using keys. Roles can be used when accessing resources. Roles can also be used for any third party accessing your resources as well. This ensures that everything is locked down in a more secure fashion than keys which need to be rotated to prevent any sort of leakage.
Key rotation can be scheduled, or it can be set on a timer. At Connectria, we use our internal tool, TRiA, which actually notifies us whenever a key needs to be rotated, either every 60 or 90 days based on the different compliance types.
Within AWS, one of our strongest tools for locking down our resources and ensuring that we don’t have any resources or instances talking to things they shouldn’t is by using security groups and access control lists. This is using those principles of least privilege so that we have everything as secure as possible. It’s important to also audit those on a regular basis to ensure that any access isn’t accidentally left open or, things like SSH, exposed.
Resource Encryption
Resource encryption is one issue that a lot of customers seeking compliance support encounter. The easiest way to encrypt your resources is to do so right off that bat, so as resources are created. Creating your resources with encryption already built-in, using AWS tools, is going to be the best way to ensure that this maintains its configuration going forward. Having to go back and re-encrypt resources that have already been deployed usually means taking those resources down, finding a maintenance window, turning off, and stopping and starting resources.
While that might not be a big deal for a non-production environment, but any time you take downtime in a production environment is going to cause issues. We really like to see resource encryption done at the start of an environment, as resources are created, making sure to be cognizant of HIPAA and HITRUST and actively encrypting as we create.
Clear resource naming and tagging are important as you’re responding to an auditor. Obviously, they are most interested in your production environment. They’re interested in the tagging of PHI. Knowing where PHI lives within your environment tells the auditor what scope they need to look at. Ensuring that we have clear tagging identifying what resources are connected to or house PHI is going to allow an auditor to see what they need to focus on in your environment and where they need to make sure controls are in place. We can also use monitoring within AWS and config to make sure that we’re maintaining all these good lockdown practices that we put in place.
The Cloud Expertise You Need at Every Step of Your Journey
The principles above represent a small collection of considerations when architecting for compliance in AWS. In my experience, I have found both resource segregation and locking down resources to be effective and beneficial architectural considerations when designing compliant AWS environments. Furthermore, Connectria is a leading AWS Advanced Consulting Partner and audited managed service provider that can help you in more ways than one when it comes to managing your cloud environments.
This article was the second in our 3-part series on Compliance in AWS.
Contact Connectria today to learn more about how we can help your organization with HITRUST and compliance in AWS. Our comprehensive suite of AWS services has helped hundreds of organizations successfully move to the cloud and free up IT resources to focus on more strategic initiatives.
Learn how to keep your AWS environments secure and compliant
Check out our latest webinar, available on-demand
Learn how the HITRUST certification transforms HIPAA requirements into action, and discover architecture principles to keep your AWS environments secure and compliant.
Keep Reading
Prepare for the future
Tell us about your current environment and we’ll show you the best path forward.
Fast track your project. Give us a call.